
One of my clients received an email this morning. On the one hand, he had the foresight to question it. Unfortunately, that wasn’t until after he had clicked the link. After doing this and realizing the error of his ways, he forwarded it to me. After I explained to him what it was, he asked me how I knew if it was legitimate or not, and that led me to thinking … maybe we should share with folks how we can identify if one of these emails is malicious or not.
First up, I’d like to state that this is the first time I’ve seen this particular scam, so this is a good one to be able to explain at least my thought process when I’m looking at these.
Below is the email in question. The names have been blurred to protect the innocent.
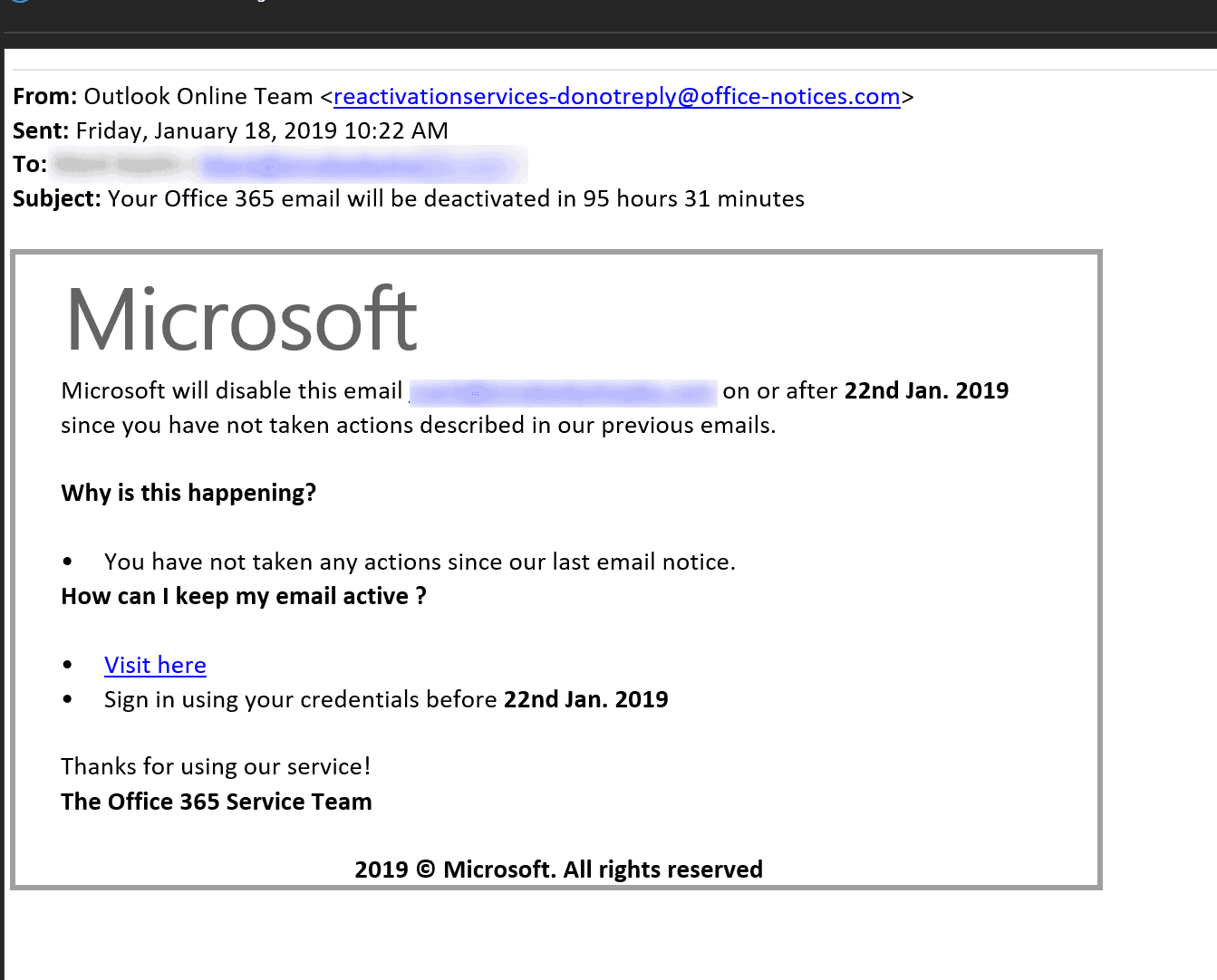 This particular email is preying upon people’s fears. It immediately makes the recipient feel like they are going to lose their account; it gives a deadline to induce a sense of urgency and gives you a convenient out. These are common tactics.
This particular email is preying upon people’s fears. It immediately makes the recipient feel like they are going to lose their account; it gives a deadline to induce a sense of urgency and gives you a convenient out. These are common tactics.
The next flag for me is the “from” address. Before we even get into the e-mail itself, this is of concern. “Outlook Online Team reactivationservices-donotreply@office-notices.com”. Correspondence from Microsoft will only come from an @microsoft.com email address.
Now onto the body of the email. It’s immediately suspect to me for a number of reasons. Look at that date format: “22nd Jan. 2019.” In the US, the common format is Month-Day-Year, not Day-Month-Year. Sure, the military uses that format, but most companies do not. Not saying they can’t or won’t, just that it’s unusual. Next is at the bottom with that copyright. That’s not a common format for the copyright, and, well, let’s just say I’ve spent enough time on Microsoft websites to know that this is their normal copyright format:
 Not to mention, they don’t generally put that at the bottom of their emails. How do I know this? Let’s just say I correspond with Microsoft a lot. I’ll show an example email in a moment.
Not to mention, they don’t generally put that at the bottom of their emails. How do I know this? Let’s just say I correspond with Microsoft a lot. I’ll show an example email in a moment.
And last but not least, and definitely the final nail in the coffin, is the hyperlink:
![]() Just sitting there, it looks all innocent, and most people don’t pay much attention when they hover over a hyperlink, but being the paranoid individual I am, I do pay attention:
Just sitting there, it looks all innocent, and most people don’t pay much attention when they hover over a hyperlink, but being the paranoid individual I am, I do pay attention:
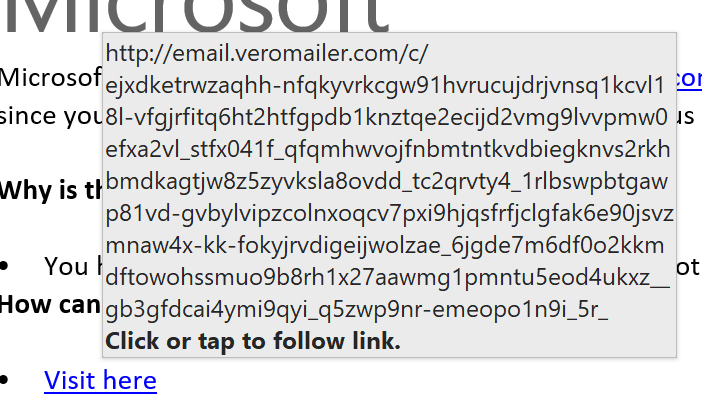
Oooh … veromailer.com and a bunch of other gobbledygook along with it! I don’t even need to do a WhoIs lookup on this one to know it’s not right. But let’s do one anyway:
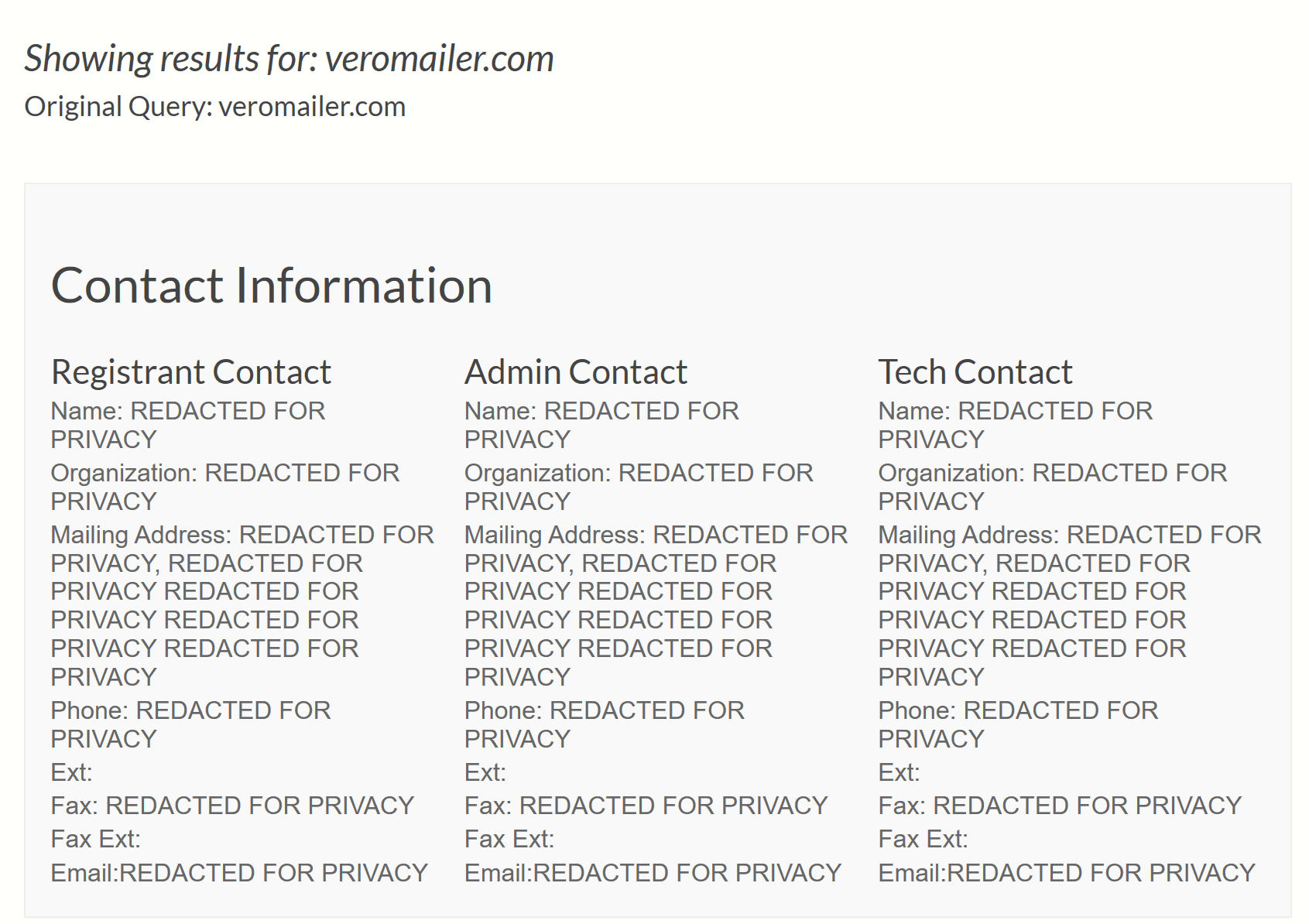 Yeah, doesn’t look too legit, does it? For reference and comparison, here’s what the WhoIs for Mirazon.com looks like:
Yeah, doesn’t look too legit, does it? For reference and comparison, here’s what the WhoIs for Mirazon.com looks like:
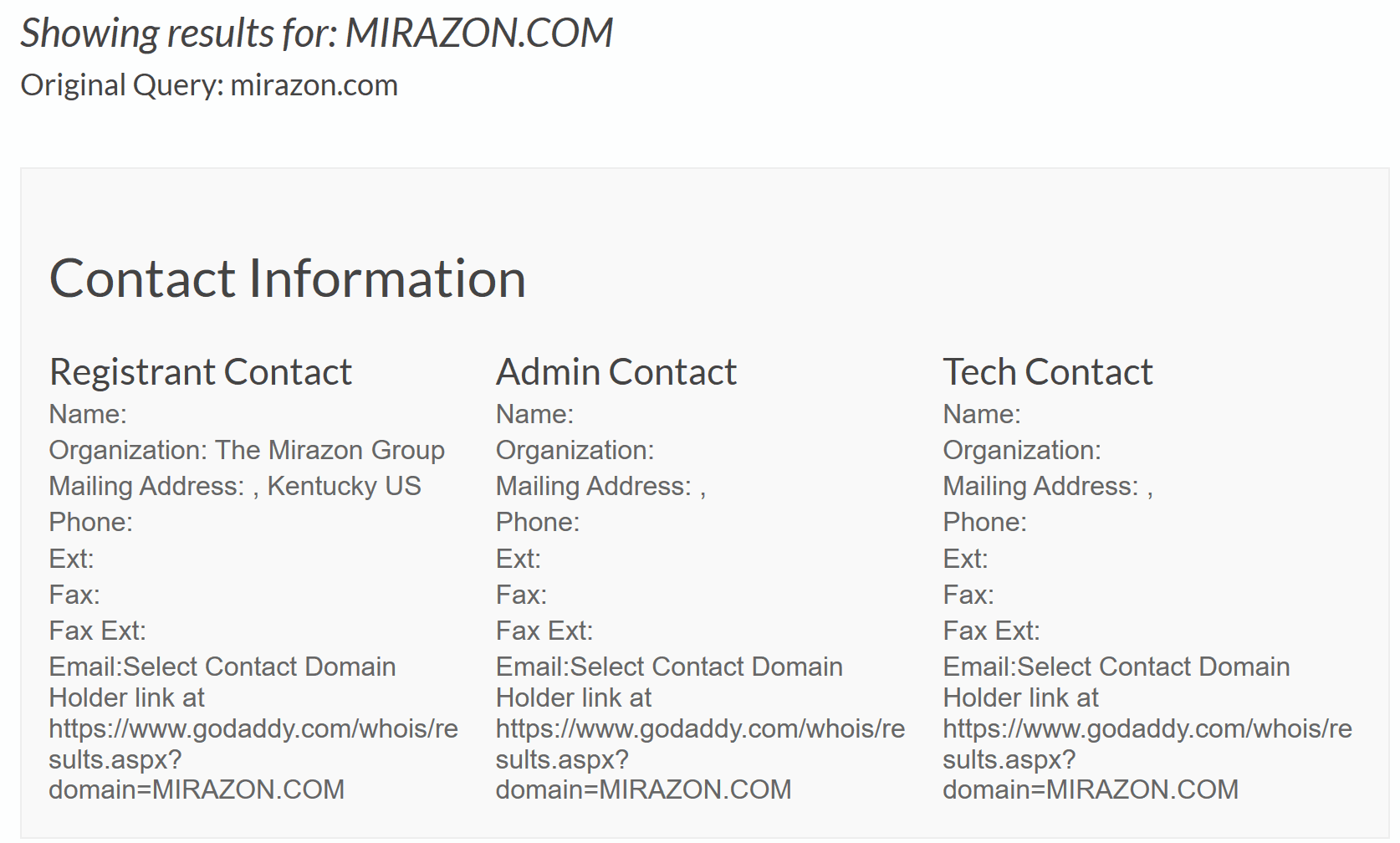 Not a whole lot of info, but not a bunch of shady “Redacted for Privacy”.
Not a whole lot of info, but not a bunch of shady “Redacted for Privacy”.
These are the warning signs. For reference, here’s a legit email from Microsoft, complete with hyperlink:
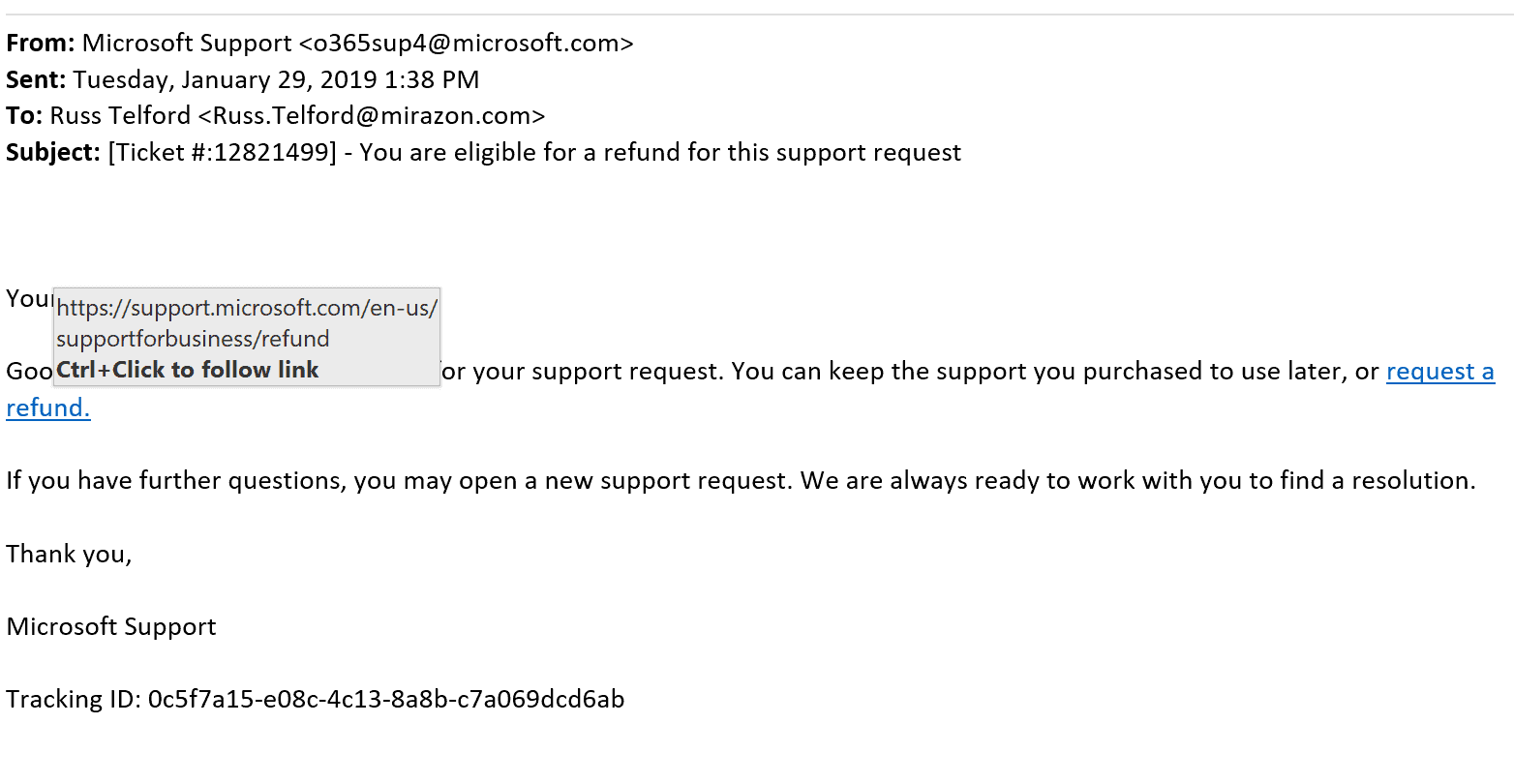 Notice the @microsoft.com email address, the tracking ID at the bottom, and the legit hyperlink? Well, there you go. Real vs. Scam.
Notice the @microsoft.com email address, the tracking ID at the bottom, and the legit hyperlink? Well, there you go. Real vs. Scam.
I really hope this has been helpful to give some insight into how we are able to identify email scams. The bad guys really do put on a convincing show and sometimes it’s rather difficult. Just remember, if there’s EVER any shred of doubt, it’s probably a scam. We’re always happy to take a look for you, just PLEASE, PLEEEEEEAAAAAAAAAAAAAASSSSEEEEE DON’T CLICK THE LINK before you ask us about it!!