Fortigate has changed a lot in FortiOS 5.2* and at Mirazon we like to experiment with new software and upgrades before we apply them to customer environments. While exploring FortiOS 5.2, I noticed that one of the things that has been changed heavily is how to set up the SSL VPN. Here are some of the ways it has changed:
- Portal creation
- Settings
- Firewall policies (for interfaces)
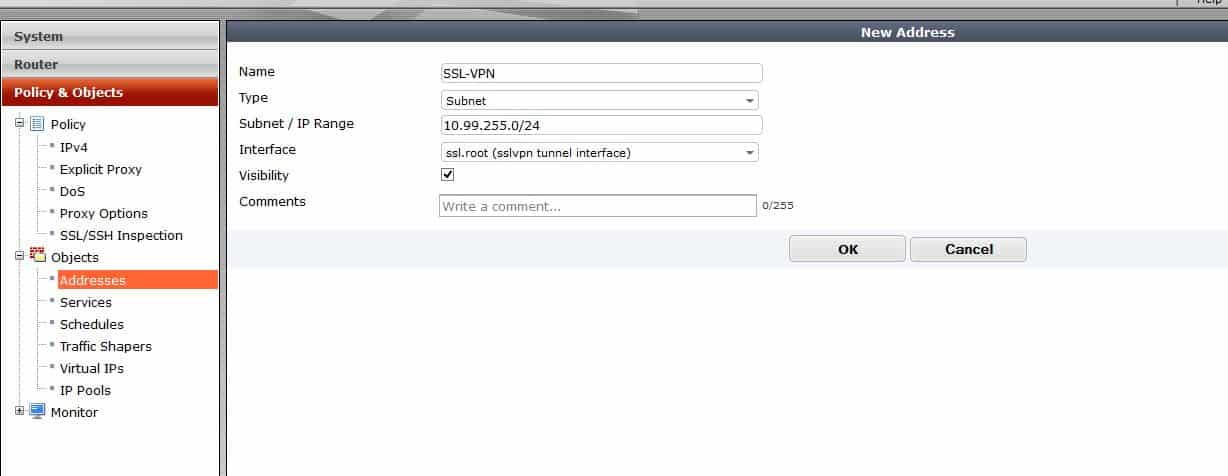
In our example, to enable and create needed policies for the SSL VPN to function, you need to create a scope 10.99.255.0/24 for the VPN subnet, and make sure your two local networks are being sent to the client’s routing table via split tunneling. Local subnets should be set to 10.32.250.0/24 and 10.32.251.0/24. Of course, these would be set to whatever is appropriate for your environment.
First, create the address object for the SSL VPN clients:
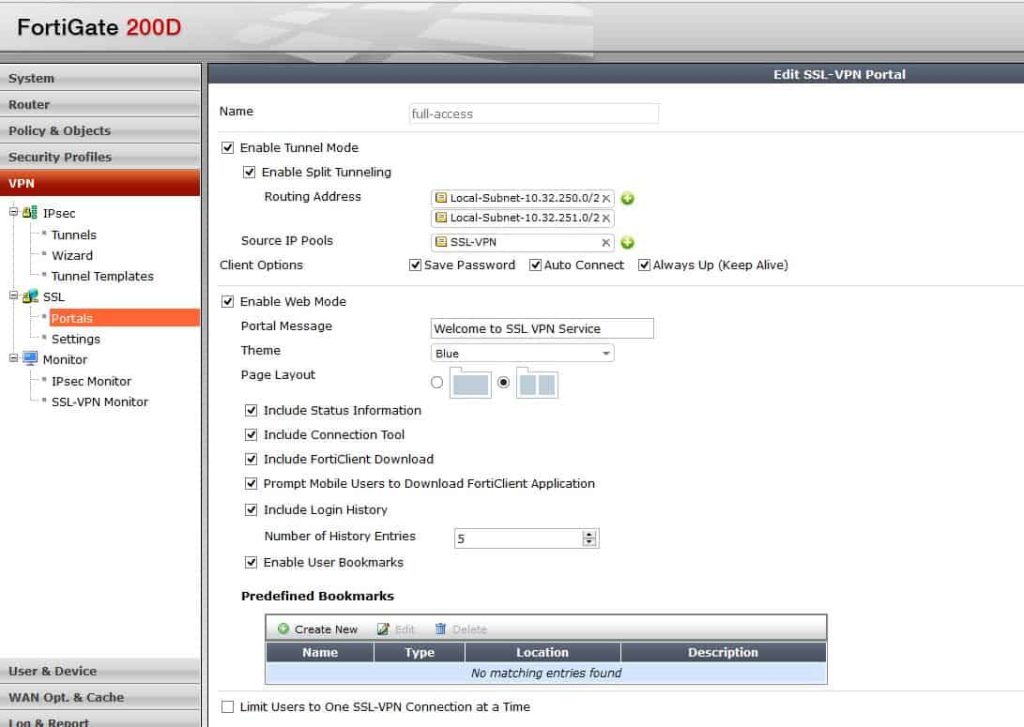
Portal Configuration
In the portal you can configure split tunnel, IP Pools, bookmarks, etc. The portal also has options to save the password and the allow more than one instance of that user to log in.
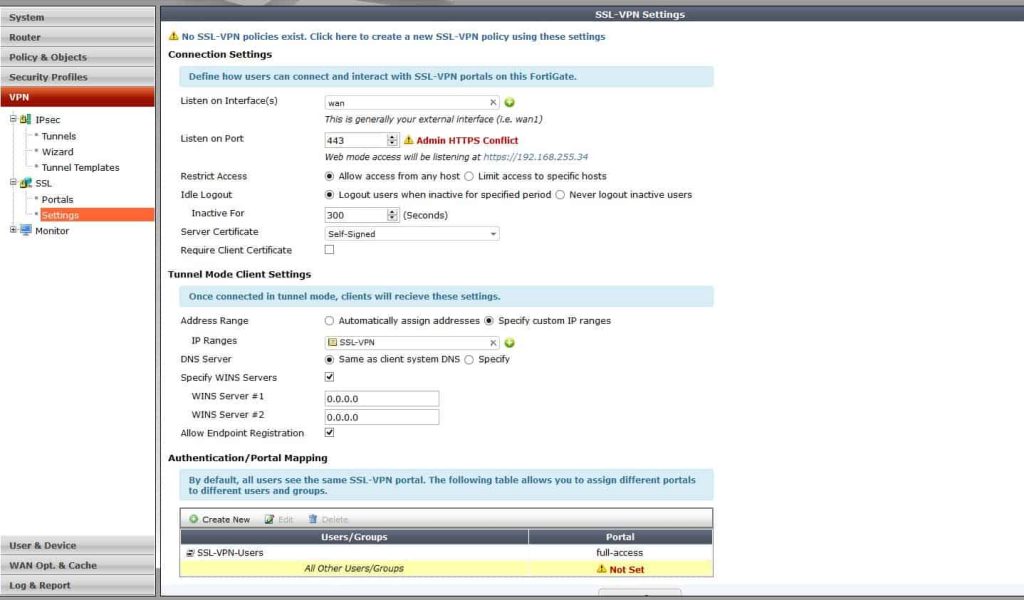
VPN Settings
Then we will start to configure settings for our VPN. Notice that it is much different than 5.0. We configure the port, VPN client addresses and who can access the VPN from here. Before it was in many different places. Also notice at the bottom there is the users who can log into this device, and what portal they will see. You can totally customize this so that domain admins get one portal and restricted users get another.
After you configure what is needed, there is a red line that comes up and says, “default users not configured”. If you only have one profile then modify this. If you have multiple portals, add the most specific first, then make the standard catch-all this profile.
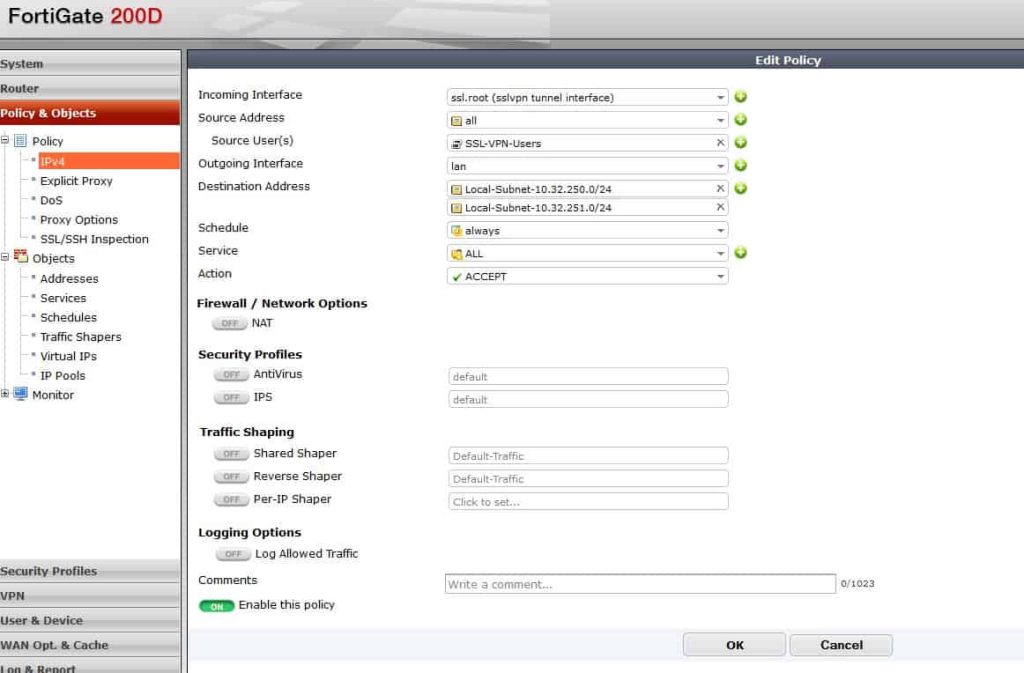
Firewall Policies
Next, create firewall policies to allow traffic to and from the VPN. This is also a big change from 5.0 where a default WAN-LAN policy was required as well as to have the service be SSL. With 5.2, that is really done in the VPN Settings page.
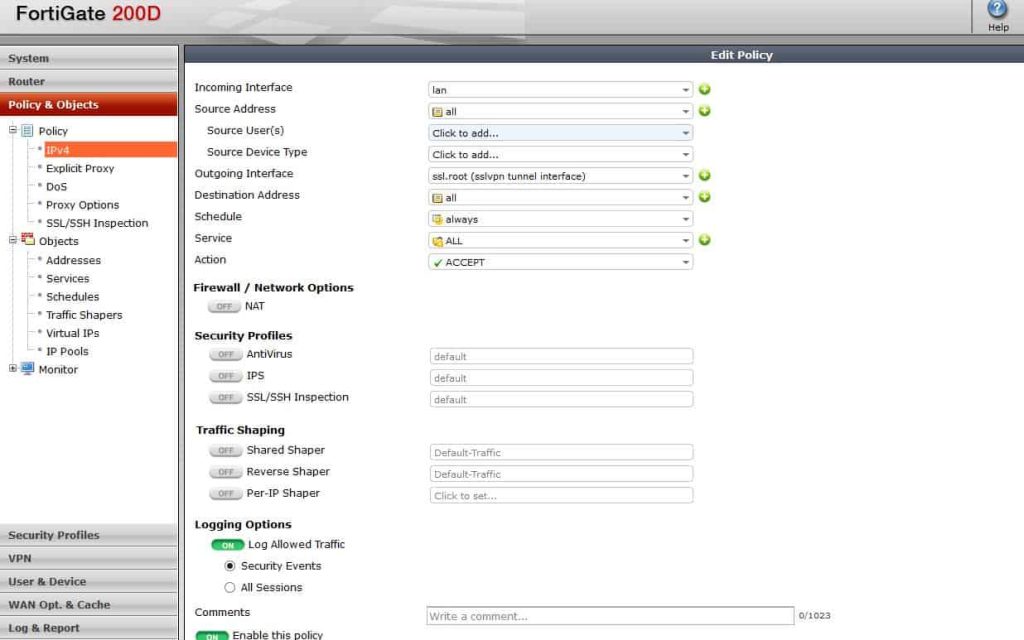
Allow VPN traffic to the LAN and make sure you are using the network address objects that are specified in the split tunnel policy under the portal. Adding the local subnets basically allows VPN clients to have access to those networks. You could use any here but I chose to use my local subnets.
From there, create the opposite of that policy to allow traffic from the LAN to access the SSL VPN interface:
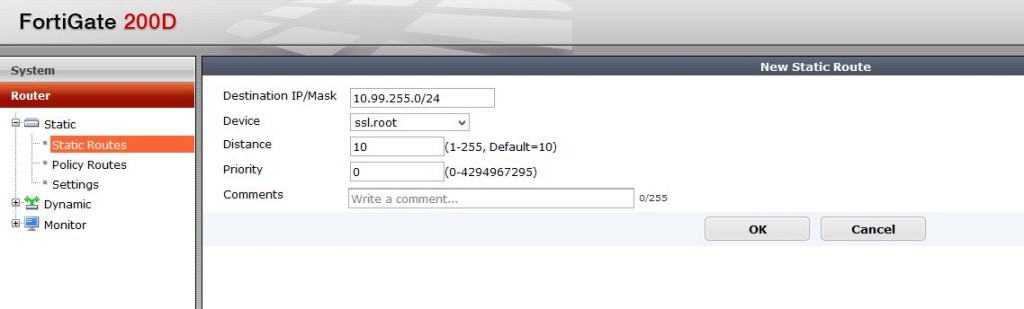
Lastly, create a route to that SSL VPN subnet:
That should be it, but there are some considerations that should always be taken into account. For one, always evaluate the security that you need. In this example I did not add any UTM or restrictions to who can access the VPN, and to what servers/addresses. Secondly, notice that in the VPN Settings page, if you are doing Forticlient registration, ensure that the option is checked so registration can be used on that interface. Another consideration should be the amount of time users stay logged into the VPN.
After enabling this, your VPN should work great!
Learn more about the Fortinet advantage.
If you’re interested in adding more Fortinet to your network or need help with your firewall, contact us today!
*The following hardware does not support FortiOS version 5.0 and above releases of software: FortiGate 30B, 50B, 50B-LENC, 51B, 51B-LENC, 60B, 82C, 100A, 200A, 224B, 300A, 400A, 500A, 800, 800F, 1000A, 1000A-LENC, 1000AFA2, 3600, 3600A, 5001, 5001FA2, 5002FB2, 5005FA2, and FortiWiFi 30B, 50B and 60B. Get in touch with us if your hardware falls in this category because it could be time to upgrade. Learn about our trade-up program.