Reach Out – We're Listening!
Have questions or need assistance? Drop us a line – we can’t wait to meet you.
Headquartered in Louisville, Kentucky, we proudly deliver world-class IT support and solutions to customers across the nation.
![]()
If you are actively suffering from a ransomware attack, call us immediately at (502) 240-0404
Were you recently the victim of a ransomware attack?
Simply want to protect your company from ransomware threats?
Don’t pay the ransom yet – our experts can help with a ransomware infection and ensure your IT environment has ransomware protection built into the systems.
Ransomware remediation is a delicate process of not only eradicating ransomware from compromised network systems, but potentially coordinating with cybersecurity insurance, forensics and law enforcement, whilst communicating with the organization’s stakeholders. This is a gradual process with many different sub-components, and each component that is impacted needs to be fixed. The persistent techniques built into ransomware make it possible for it to remain on computers without being completely removed — this makes removing it particularly challenging. Wiping the afflicted machine or restoring its data from a backup are the two most efficient ways to get rid of ransomware.
But sometimes this isn’t always possible.
Regardless of your situation, we’re here to help. Whether it be ransomware detection, ransomware remediation, ransomware protection, or ransomware prevention, our experts have the knowledge and resources to mitigate/prevent a widespread ransomware attack and ransomware infection.
The first line of defense against a malware attack and/or viruses is ransomware detection. Until files are blocked or encrypted, ransomware remains undetected on a compromised computer. Most of the time, victims are unaware they have malware until they receive a ransom demand. Ransomware detection identifies the infection sooner, allowing victims to take action before irrevocable damage occurs. By detecting ransomware quickly and maintaining a regular backup routine, you won’t have to wait for an undependable decryption key to restore your system. As a result, your files might never be lost.
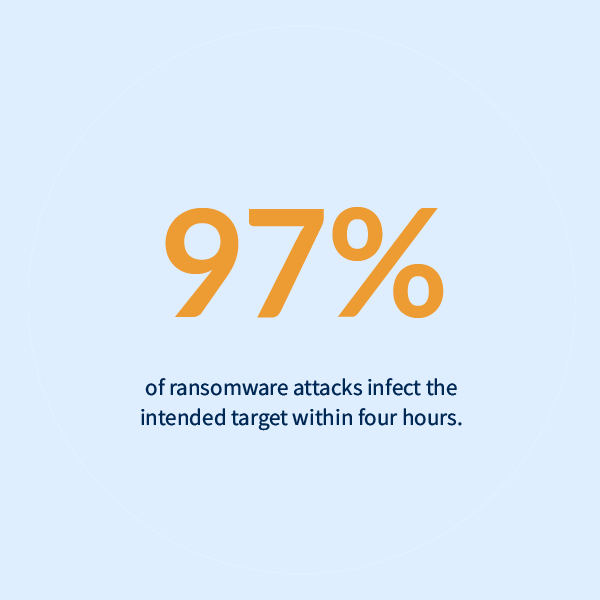
Recovery from a ransomware attack is – at best – difficult and time-consuming. It can cost a lot of money for any business to determine the extent of the attack, find the most recent clean data, and recover rapidly while also making sure that your backups haven’t been destroyed or encrypted. Many organizations go back and forth trying to decide if they should pay the ransom or not, and it can feel like you’re stuck between a rock and hard place.
Jump into action with our multi-talented experts, who have experience cooperating with the FBI and cybersecurity insurance, extensive knowledge about ransomware decryption tools, and expertise in ransomware removal with a variety of different strains (CryptoLocker, WannaCry, LockBit, and more).
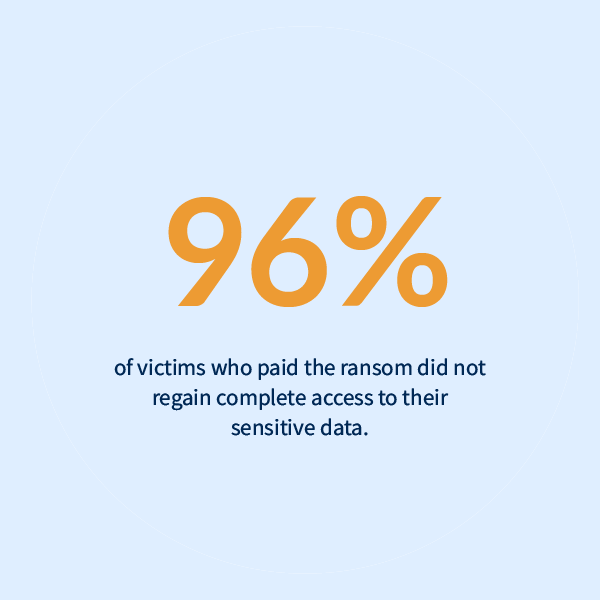
To successfully combat ransomware and have effective ransomware protection, it’s more crucial than ever to secure the most vulnerable areas of risk – endpoints and cloud workloads, data, and identity – and stay ahead of the cyberthreats in today’s world. This includes antivirus, network security protocols, email security protocols, other security software, and more on a range of devices – computers, tablets, mobile devices – you get the idea. Our experts can ensure you follow insurance requirements and give you peace of mind knowing you’re protected. Afterall, you never know when or where the next attack may come from.
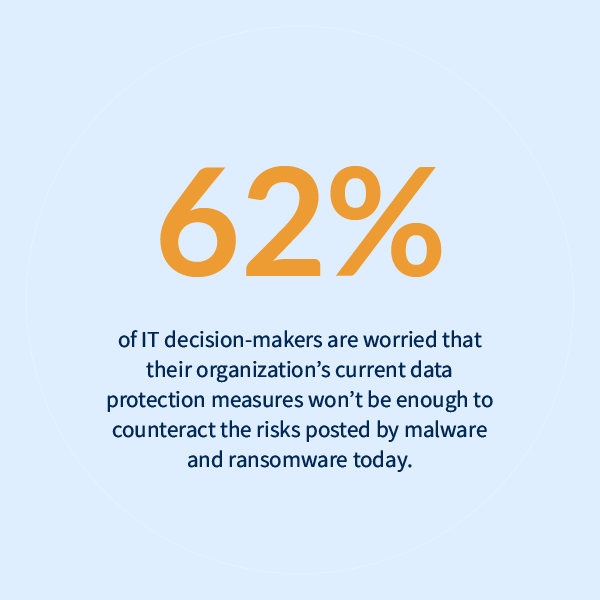
The script consumes system resources in order to execute searches and encrypt files.
Attackers install numerous tools to assist them in exploiting vulnerabilities and performing other important activities.
Coming into and leaving the system as the ransomware script interacts with the Command and Control (C&C) Server.
The ransomware software hunts down and creates encrypted files in your system.
Ransomware makes modifications to security settings in an effort to prevent surveillance operations.
Attackers enact a plan of preventing the victim from restoring their data by crippling backup operations.
Privileged account creation enables the attempted ransomware infection.

Download our
Free Layered Security Strategy Guide!

"*" indicates required fields
Cyber big game hunting is a form of cyberattack that frequently uses ransomware to target important, high-profile organizations or high-value enterprises. In general, victims are selected based on their financial capacity and likelihood of paying a ransom in order to restart business operations or escape public scrutiny. Big game hunters use a range of tactics to carry out their attacks. The most common technique is ransomware, a sort of virus that will encrypt files and demand payment to decrypt the stolen data.
Common targets include:

Whether you’ve dealt with a ransomware attack in the past, are currently dealing with one, or are just trying to prevent ransomware attacks from happening – we understand how stressful and overwhelming it can be. Where do you begin? What are the legalities involved? How do you begin to remedy ransomware attacks?
When you work with Mirazon, you can expect our experts to be an extension of your team. We make you, your employees, company, and IT environment our top priority – just as you would.
Headquartered in Louisville, Kentucky, we proudly deliver world-class IT support and solutions to customers across the nation.

Remediation | Protection | Prevention
An incident response plan enables businesses to act swiftly and efficiently in the face of a stressful scenario involving threats, disruption, or disaster – which can impact the organization’s operations on all levels – and are designed to address scenarios that endanger digital assets and data access. The level of importance of having this type of plan cannot be overstated because should an incident occur, the people who will be dealing with it might be at their worst – stressed, underslept, afraid, and emotionally spent. Creating a comprehensive plan that everyone is familiar with ahead of time will mitigate decision fatigue, mistakes, and delays when the “IT” hits the fan, so to speak.
As your dedicated ally in ransomware incident response, we can lessen the harm done by an attack, get your operations back up and running, and reduce the likelihood of future threats.