
In the world of secure digital communication, Microsoft Exchange plays a pivotal role in managing emails and collaborations within organizations.
In our previous Exchange Security Unveiled blogs, we covered essential aspects of strengthening your Exchange setup, including MFA, antivirus protection, spam filtering, and more in part one. We then talked about SPF, DKIM, and DMARC records, as well as firewalls in part two.
Now, let’s build on this foundation as we enter a critical phase of Exchange management. In this blog, we’ll focus on two key pillars: keeping your servers up to date and securing client connections, along with best practices for managing emails responsibly. (If you’re not using an on-premises Exchange server, you can skip the server updates section).
Server Updates
First and foremost, ensuring your server stays updated is critical. This involves keeping up with both Windows and Exchange updates. While many Exchange security updates come bundled with Windows updates, it’s important not to solely rely on this. Larger Cumulative Updates, for instance, require manual downloads. To stay in the support loop, you should aim to be just one update behind the latest release.
But how do you confirm this? Personally, I use a trusted command from Microsoft and cross-verify the build number on a designated web page. You can find Exchange Server build numbers and release dates here.
Get-Command Exsetup.exe | ForEach{$_.FileVersionInfo}
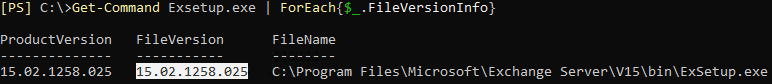
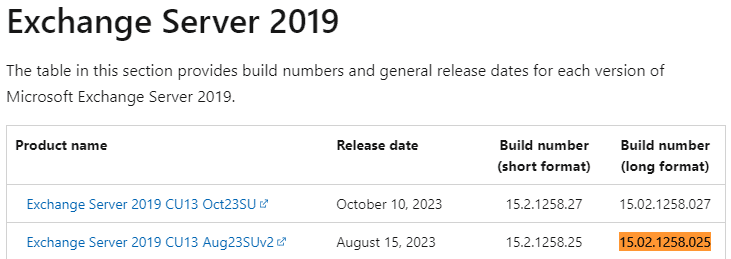
This tells me the server is one security patch behind and it’s time to schedule its installation.
Before proceeding with an update for Exchange, it’s essential to thoroughly read the release notes to gain valuable insights. Additionally, valuable information and best practices can be found at the Exchange Team Blog.
When installing updates, always ensure to do so from an elevated (Run as Administrator) CMD prompt, even if UAC prompts are not displayed. This precautionary step is crucial in preventing potential issues that could arise during the update process.
Furthermore, it is highly recommended to run the Exchange HealthChecker after each update. This tool provides valuable assistance by identifying actions needed to enhance the server’s security, ensuring a robust and secure Exchange environment.
Client Updates
In both small and large environments, there’s a common misconception that Outlook is up to date when it often isn’t. Many users claim, “Yes, we keep our workstations fully patched.” However, it’s essential to validate this, especially before an Exchange upgrade.
Older versions of Outlook might not function properly with newer Exchange builds, potentially causing upgrade projects to fail. One of my initial checks, when users face Outlook issues, is to verify the Outlook build number.
Surprisingly, more than 90% of the time, the build is outdated. Updating the computer with Office patches usually resolves the problem. An advantage, and sometimes a challenge, of Office 365 is its automatic background updates. Exchange logs provide insights into the Outlook versions used by users, facilitating effective management of upgrades and updates. We’ll delve deeper into this in our next post.
Client Connectivity
When dealing with former employees and their mailboxes, a smart approach is converting their mailbox to a shared mailbox. This action not only retains the mailbox, but also disables the user account (if on-premises) and frees up Microsoft 365 licenses.
The great part? A shared mailbox doesn’t require a license.
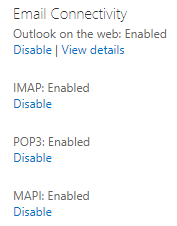
Exchange offers multiple client communication methods. Some can be configured at the server level. However, managing a mix of these methods can be a challenge. For instance, if you prefer only 30 users to use OWA, you can navigate to the Exchange Admin Center or use PowerShell.
In the Exchange Admin Center, you can configure Email Connectivity by accessing the mailbox features. However, it’s important to note that this method doesn’t cover all possible connection methods.
Managing Client Connectivity
Using the Set-CasMailbox command, you have the power to control various client access methods like OWA, ActiveSync, ECP, EWS, MAPI, IMAP, and POP. However, as staff members join or leave and job roles evolve, maintaining these settings manually becomes a challenge.
To address this dynamic environment, I’ve devised a PowerShell script. This script efficiently enables or disables these connection methods based on users’ group memberships, ensuring users have access only to the methods they require.
Remote PowerShell Access
One crucial setting, specifically controlling access to Remote PowerShell, can only be handled through PowerShell. By default, Remote PowerShell access is enabled for all users, which is technically convenient.
However, from a security standpoint, this raised concerns. Notably, in the past, disabling this access for all users was a necessary measure to counter an ongoing exploit until Microsoft could release an update to secure and restrict this feature.
Securing Remote PowerShell
I strongly recommend securing Remote PowerShell access for all users. Typically, users aren’t familiar with PowerShell, making this precaution essential. However, exercise caution to avoid accidentally locking out administrative accounts. If inadvertently locked out, restoring this access involves a few tricks.
The challenge arises because the Set-User command, an Exchange command, manages this feature. If you lose access to Exchange Management Shell, running Exchange commands becomes impossible.
Should you need assistance with this workaround, please reach out, and we’ll guide you to restore your permissions.
SMTP Relay Best Practices
In simple terms, it’s essential to avoid having wide-open SMTP relays. We all understand the risks associated with this on the internet, but it’s equally crucial to steer clear of this internally. While having an open SMTP relay may not pose a direct security threat, it can severely impact your organization’s reputation. Unchecked relays could lead to legitimate emails being blocked due to spam-like behavior. In fact, we’ve witnessed Microsoft 365 locking down entire tenants for hours due to excessive emails being sent.
If your organization has an open relay internally, I strongly advise reaching out to Mirazon. We can assist in enabling and analyzing the logs available. This process helps identify legitimate sending users and IPs, enabling necessary measures to prevent unwarranted lockdowns based on these identified patterns.
Conclusion
In this journey of fortifying your Exchange environment, we encourage organizations to proactively implement these insights and best practices. Should you require assistance or further guidance, especially with the mentioned PowerShell workarounds or SMTP relay management, don’t hesitate to reach out. Together, we can build a robust and secure Exchange infrastructure, enabling seamless communication and collaboration within your organization.
Stay tuned for the next installment in our Exchange Security Unveiled series – Part 4. We’ll delve into vital areas to monitor and guide you on setting up effective alerts to ensure a secure Exchange environment.
If you’d like to learn more about Exchange security, PowerShell workaround, or SMTP relay management, please contact us by calling (502) 240-0404 or emailing info@mirazon.com.
