
These days we are having a lot of conversations about security. Typically, these conversations are centered around technical solutions. We discuss the latest in Next-Gen AV/EDR, Firewalls, and more frequently, Multi-Factor Authentication; and for good reason. It was just under three years ago that Microsoft proclaimed that MFA stops 99.9% of all attacks on your accounts. Well… that was three years ago.
A recent story from Ars Technica reports on an on-going phishing campaign where attackers have been able to by-pass Microsoft’s Multi-Factor Authentication. The campaign launched in September 2021 and has targeted over 10,000 organizations to date.
In short, the attackers set up a phishing website that appears identical to the familiar Microsoft login page. This part is not new and is easily defeated by MFA. In this new campaign, the threat actors’ phishing site is acting as a proxy between the end user and Microsoft. When the user enters their credentials, the credentials are sent to Microsoft. When Microsoft sends the MFA challenge, the phishing site sends the challenge to the user. Once the user is authenticated, the phishing site steals the users’ session cookie. The threat actors now have access to the end user account.
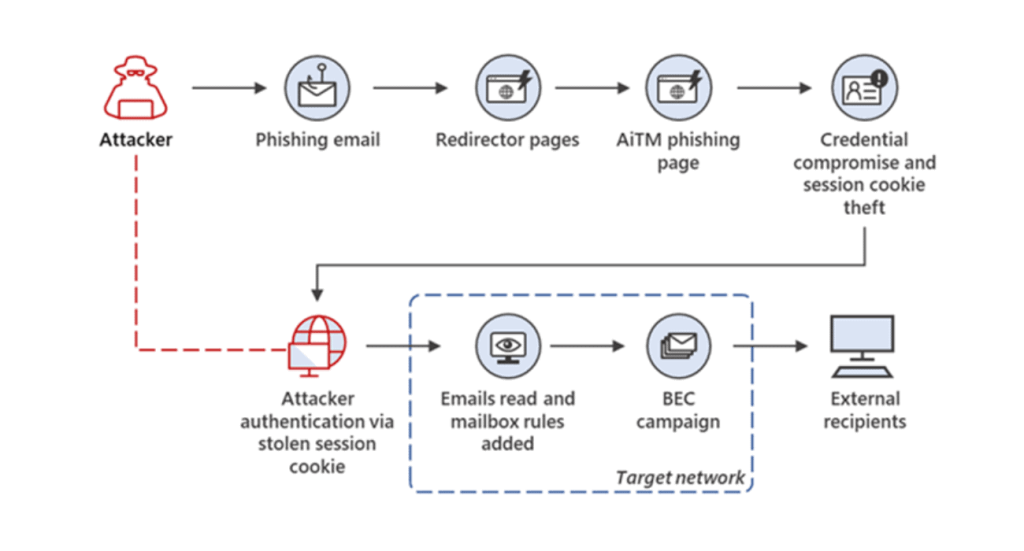
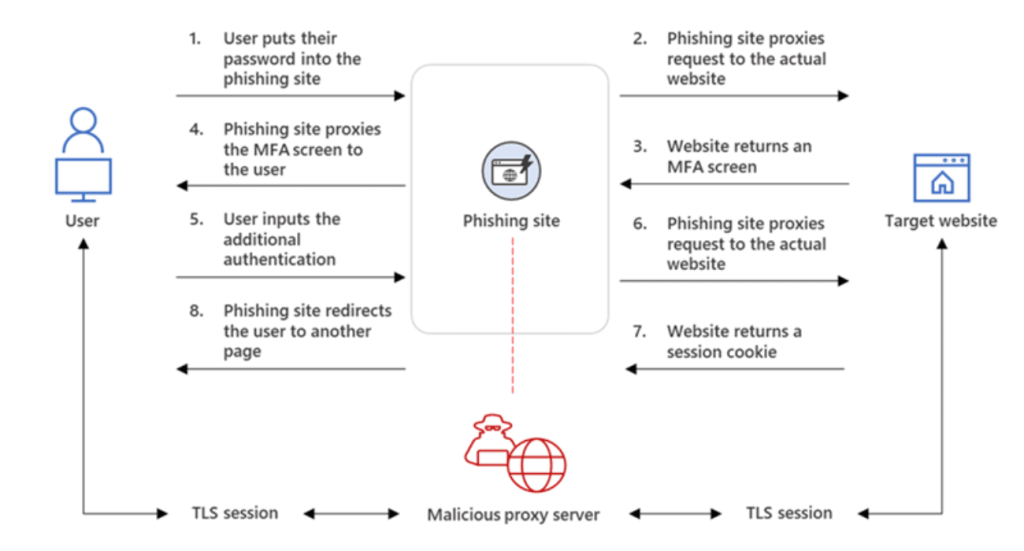
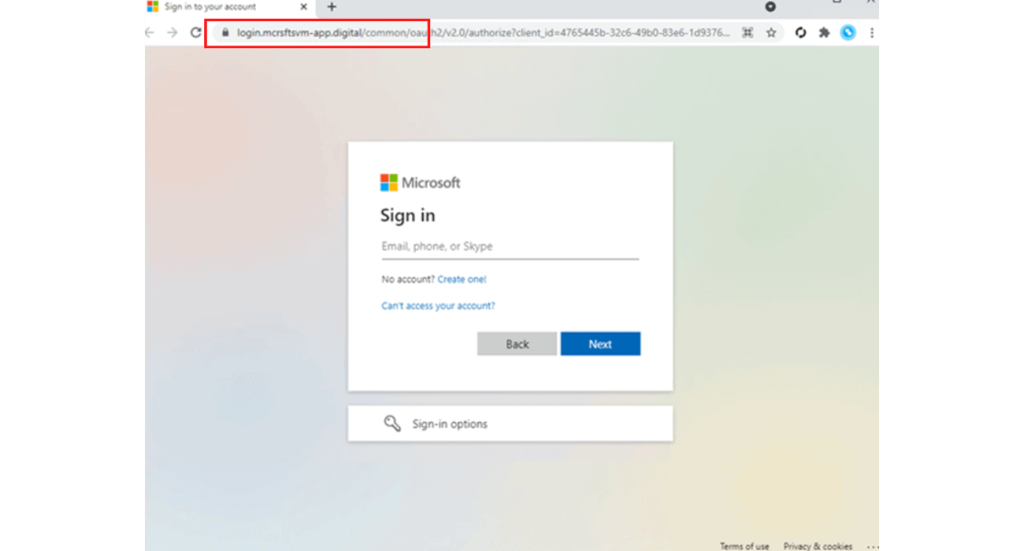
This is a very clever workaround, but not a huge technological marvel. The attackers did not discover some vague vulnerability to exploit. Instead, they relied on a tried-and-true tactic. They hit the unofficial eighth layer of the OSI model, people. When over 90% of all cyberattacks begin with phishing, it’s hard to NOT go back to that well.
MFA protects our accounts even if we are tricked in to giving up our credentials. But if you can trick someone in to giving up their credentials, why not trick them in to giving up their MFA tokens? It’s simple really.
Microsoft has released some good information for reducing your vulnerability to this type of attack. Additionally, you can use solutions like Firewall and DNS based filtering to deny access to phishing sites. It outlines the need for a layered approach to security.
Most importantly, this attack further demonstrates the need for Security Awareness Training. SAT is often overlooked or treated as a one-off exercise. When done right, security awareness training is an on-going operation. End users need to be educated and quizzed on the most recent scams and attacks. Afterall, your users are the most targeted part of your network.
If you have any additional questions or concerns, please call 502-240-0404 or send us an email at info@mirazon.com.