
Your size does not always dictate your need or desire for enterprise-grade performance and security. Luckily, it’s possible to implement these types of features in single-firewall environments. For example, if you need to increase your internal network security but have too limited a budget for multiple firewalls, utilizing one FortiGate will not only cost effectively segregate your networks with added security, but reduce administrative complication.
Additionally, utilizing Fortinet Single Sign-On (FSSO) you can not only monitor internal traffic more granularly, you can implement policies by domain user groups. You can easily grant or block access to any firewall objects you create, such as networks or single hosts, as well as individual domain users. Fortinet’s OS is very conducive to configuring internal traffic segmentation. It has a user-friendly GUI for easily viewing policies, setting up reports for individual user traffic and has extensive troubleshooting features.
Imagine you have two subnets, one for your users and one for your servers and another company acquires you and has different compliance rules that you need to quickly implement on your network. Your new ownership requires that users from each department may only access the resources that they need to function, not only at domain level, but at the network level as well. If you have a FortiGate, you can easily utilize your existing domain groups and grant or deny access to individual servers as well as specify protocols. This will also generate logs that will provide you with user names tied directly to individual sessions to your internal resources.
There are many use cases for internal segmentation, the above example being the most common that we see. Below we’ll walk through how to set this up. As always, if you have further questions about whether or not you need this type of setup or want help configuring it, you can call us.
Some final considerations before we get into the how-to: if your network is currently in a growth stage and you think you may find yourself expanding it (a good sign is if you’re running out of IPs), then you may want to reconsider using this functionality and redesign your architecture. Additionally, if you’re in the market for your firewall and you know you’ll want to do internal segmentation with it, you may want to consider buying one that is scaled slightly above your needs to reduce latency and load on the unit.
How to Set Up Internal Segmentation on a FortiGate
First, set up interfaces on your FortiGate for both networks. In this example we will be using a Fortigate 60E on FortiOS firmware version 5.4.5.
Create an interface for your servers. Go to Network > Interfaces.
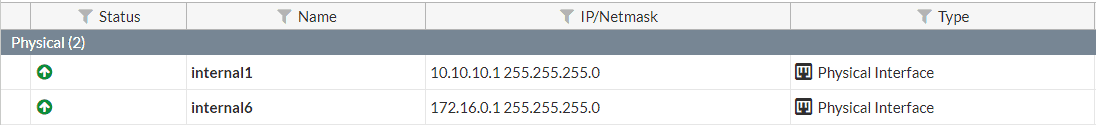
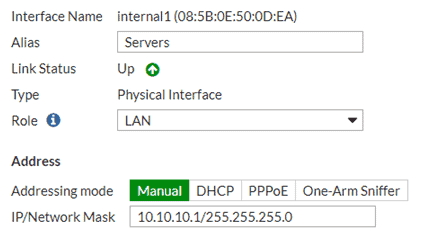
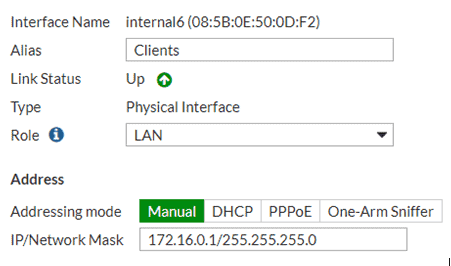
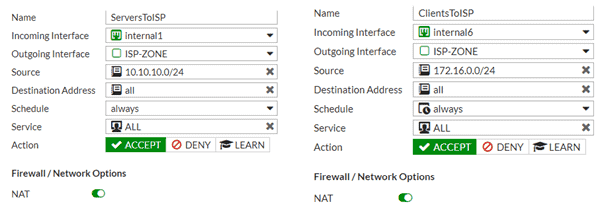
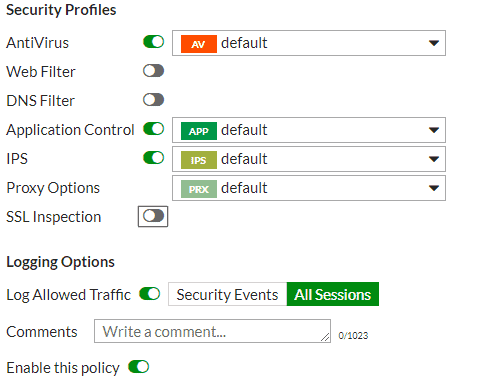
You can specify services that allowed or block specific actions. Utilizing Unified Threat Management (UTM), you can process anti-virus or application filters against this internal traffic.
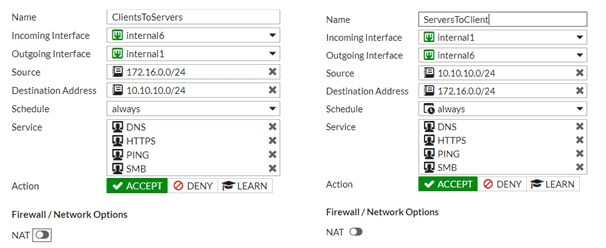
Additionally, you can enable expanded authorization and accounting options by utilizing Fortinet Single Sign-On (FSSO). This will allow you to grant or deny access to server resources by user group or machine group all the way down to application level. You will also see usernames and machine names instead of IPs in firewall logging.
Config t
vlan 172
name Clients
exit
vlan 10
name Servers
exit
I have given each interface an IP address just for pinging in this example. Since this is a Layer 3 switch with routing, I can have multiple IPs. If this is an option, I recommend making VLAN interfaces on the switch.
interface vlan 172
ip address 172.16.0.2 255.255.255.0
exit
interface vlan 10
ip address 10.10.10.2 255.255.255.0
exit
interface range gi 1/0/1-12
switchport access vlan 172
switchport mode access
exit
interface range gi 1/0/13-24
switchport access vlan 10
switchport mode access
exit
interface range te 1/0/1-2
switchport access vlan 10
switchport mode access
exit
That’s all there is to it! You now have segmented your servers from your users with a FortiGate 60E and a switch using only layer 2 service. The same principle is easily done with two switches; one for your clients and one for your servers.
If you’d like a full diagram of this architecture and the corresponding configurations, fill out the below form!
Oops! We could not locate your form.