
Thanks to Log4J, AKA the vulnerability that has much of the IT world in panic mode, 2022 is set to start towards an unfortunate bang.
Just when we think everything is under control, another exploit is found – the most recent as being reported on December 28, 2021. Researchers at Checkmarx discovered a way to use Log4j to launch malicious code.
What does this mean for you?
Before we get started, make sure to patch Log4j.
Important Note: Even if you have already upgraded to version 2.17.0, this one is vulnerable too. The most recent “secure” version is now 2.17.1.
Events like these illustrate why endpoint security is so important. And just as important, is selecting the right endpoint security platform. These systems guard against malicious cybersecurity threats to network-enabled devices and serve as the front-line in defending your network. When choosing an endpoint security product, there are several factors to consider:
- Price
- Performance
- Features
Too often, the team behind the product gets overlooked. Several teams, such as Trend Micro, have released scanning utilities that scan your network for vulnerable systems. This is a valuable solution and should not be left unnoticed.
But what if you had a powerful platform that could begin mitigating issues within hours of them being noticed? And then, what if the team behind that platform could deliver the pertinent information directly to you?
That’s even better. Enter CrowdStrike.
Within hours of the Log4J announcement, CrowdStrike’s engineers released queries to the public to help root out Log4J vulnerabilities and potential victims. These queries were announced through social media, and the users of CrowdStrike were able to query their entire organization to find vulnerable systems within seconds:
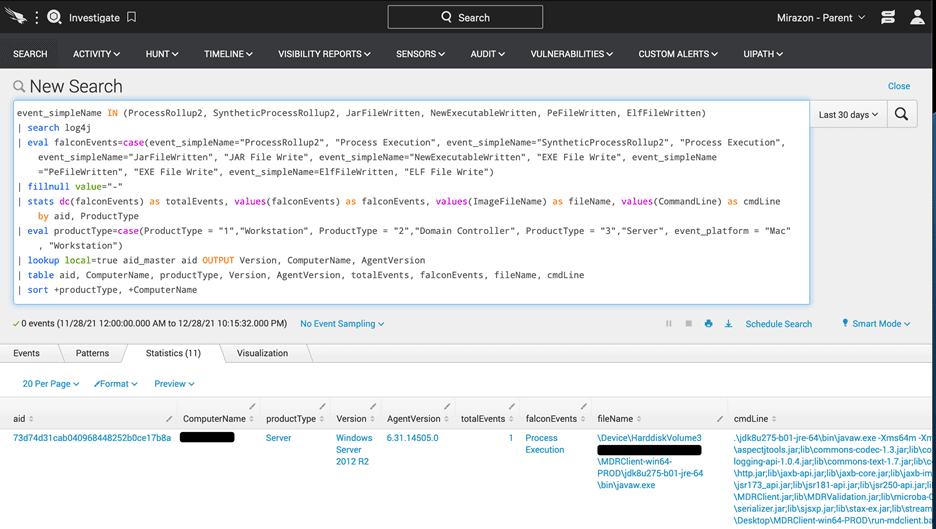
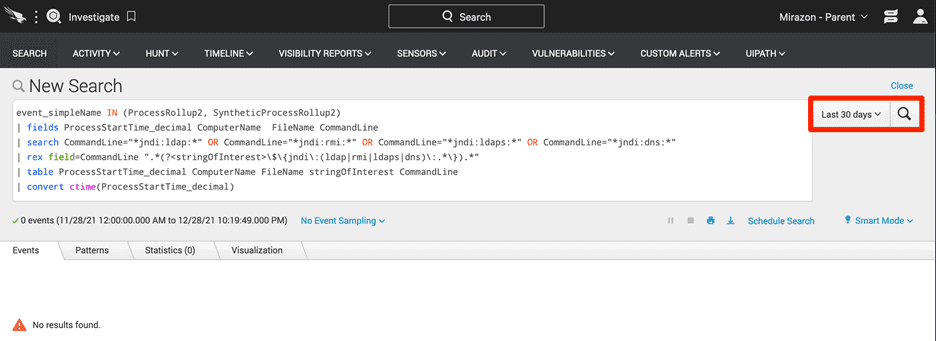
CrowdStrike does not. Telemetry data for all systems is uploaded for analysis constantly. This allows you to collect data in preparation for things that have not even happened yet. The data is always there when you need it.
Keeping your IT systems and business protected is increasingly important in this day in age, and having a team you can trust to have your back is just as crucial. Follow these tips and guidelines to get a head of your vulnerabilities.