
Ransomware has undoubtedly made a name for itself over the past few years. It’s all over the news and the Internet, and it’s certainly earned a prominent place in our concerns. Even though ransomware has been around for a while, there are still only three ways to deal with getting compromised: restore from backups, you (or your insurance) pay the ransom and hope it works, or cut your losses and lose the data. But if you take action to stop a ransomware attack in its tracks, you could spare yourself a great deal of pain.
As a result, our preventative strategies always appear to lag behind. Because of this, we frequently overlay a variety of technologies and tactics to safeguard against damaging data loss brought on by ransomware. As with everything, the saying “An ounce of prevention is worth a pound of cure” applies to ransomware.
You can learn more about this and the services we offer by visiting here.
Prevent & Protect
As the saying goes, an ounce of prevention is worth a pound of cure.
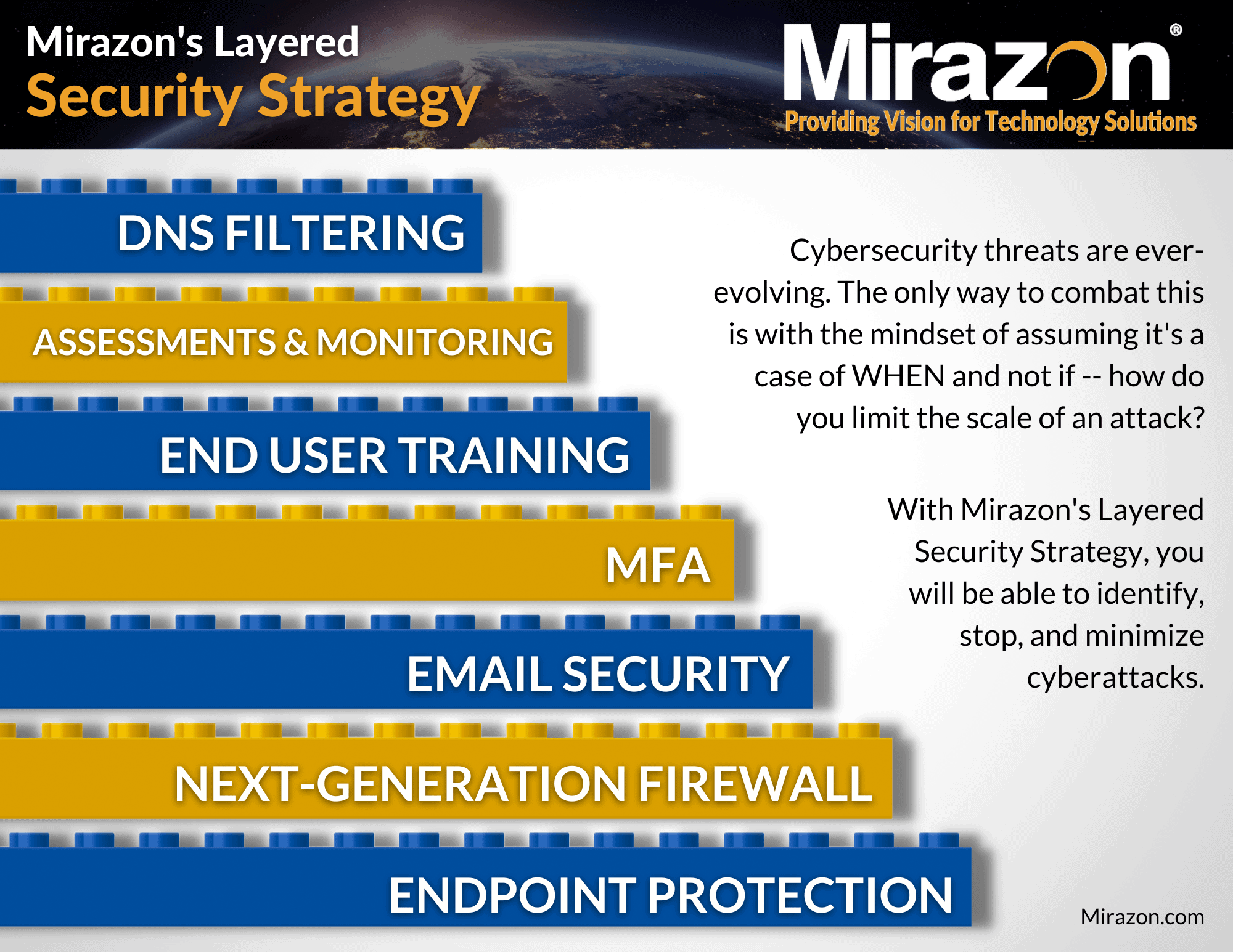
Have A Multi-Tiered IT Security Strategy
What does this mean? In a nutshell, DO NOT rely on just one point of security, such as a firewall or anti-virus. Instead, there needs to be security between your users and possible attackers at several levels. Anti-virus, firewalls, email security, DNS protection, user rights all play a role in your security.
If something were to infiltrate your network, your defense security strategy – which includes firewall, antivirus, content filtering tools, and more – can help you rapidly identify unusual behavior and keep out anything malicious. In order to limit the spread of ransomware, your network architecture should be designed so that not everyone can access everything. It’s crucial to realize that no single measure will totally safeguard you, but rather a combination of solutions and behaviors that work together to keep you secure.
Patches, Patches, Patches
Keep everything up to date. Switches, servers, firewalls, anti-virus software – everything. You should have a regularly scheduled maintenance window in place where you can get problems patched. The vast majority of reported vulnerabilities are resolved with patches.
Endpoint Security
It goes without saying that you should keep your software updated, but you should also review your features and policies. Today’s anti-virus software comes with capabilities and policies that prevent encryption and other ransomware-related operations. They often are not enabled by default.
Close Remote Desktop Protocol (RDP) and Other Services
Be cautious about the services you expose to the public Internet. The risk of leaving RDP open to the Internet is too great. Yes, even if you use a non-standard port. Instead of leaving RDP open, there are now other, better choices for remote access.
Email Security
Most security vulnerabilities today have less to do with firewalls and packets and more to do with exploiting end users. Email is the most convenient way to contact your end users. Use a provider that provides email security, such as Proofpoint.
Speaking of Users…Educate Them
Knowing is half the battle. They weren’t given the name “computer viruses” for nothing; they propagate, infect, become smarter, and evolve. Stay educated on what’s out there. As the threats change, your security strategy must too. Teach employees to be suspicious, not to click on things, and not divulge personal information.
End-user training is key. Ransomware typically infiltrates networks of businesses by tricking the end user through spam emails or malicious websites. It’s crucial to continuously educate your users on how to spot these rogue actors, and to establish an open-door policy so that people feel comfortable reporting an error right away. Security Awareness Training (SAT) here.
Let Your Firewall Be All It Can Be
Most firewalls today come with a suite of unified threat management (UTM) technologies to go above and beyond and create a layer of protection between your systems and the outside world.
Gap Your Backups
Air gap (having a backup that is off your network and inaccessible) or logic gap (leaving backup systems off your domain, in the cloud, etc.) is a must in today’s environment. This is due to the fact that ransomware viruses are becoming smarter and are now able to map all devices connected to your environment and encrypt them. As a result, your backups will be rendered useless if the ransomware can access them.
Have Backups
Let’s face it, even if you do all of the procedures I’ve listed here and more, it’s still possible that you’ll be infected with ransomware. You must set up a reliable backup AND restore system. A very key element to surviving a ransomware attack, however, is your backups.
Paying into this criminal organization isn’t ideal because you can’t rely on them to truly decode all of your data after you pay them. In the event that you do encounter ransomware, your backups will allow you to restore your data without having to go through all of that – saving you time, money, and sanity.
Remediate
Stop Any Access To/From Outside
It’s common for ransomware and other malware to try to phone home. Threat actors do this for a number of reasons, either to start encrypting your computers (if they have not already), transfer sensitive data offsite, or build botnets out of your systems. We normally prefer to accomplish this through the firewall, where we update the policies to restrict all sources, destinations, and services… deny, deny, deny. However it’s accomplished, the goal is to disrupt the attackers’ ability to have control of your systems.
You might be thinking, won’t this effectively create a systemwide outage? And yes, it will. This is going to take everyone off the Internet, and this can lead to a hard conversation with your company’s leadership. Business operations must halt while you adequately mitigate this. Trying to do business as usual can lead to even more damage. Remember, “Jaws” would have been 45 minutes long if they just closed the beaches.
Quarantine Systems
Because malware spreads over your network, it’s crucial that you also disable connectivity within your company. The rudimentary way to stop the flow of data across your network is to unplug it. If your network is more sophisticated with segmented networks, you can use that to your advantage.
Start identifying infected machines. To give infected and dubious PCs access to internet services, we like to build up a temporary network. This enables us to monitor the behavior and also allows endpoint security services to assess and evaluate the systems. Additionally, it keeps them separated from the clean systems.
But here’s the bottom line: you should not have ANYTHING on your production network that is not totally verified as clean.
If there is any doubt about a system, listen to Ripley:

Verify and Secure Critical Systems
If you call us and tell us you have ransomware and need assistance, the first thing we’ll ask you is whether or not you have reliable backups that are isolated from the domain. If you have backups but they’re on the domain, stop reading this and remove them from the domain. Anyone, not just those currently affected by ransomware, is subject to this. Do you have a domain joined backup server? Go remove it from the domain, I’ll wait.
If you don’t have reliable backups, this is a problem. All your line-of-business servers, including your ERP, CRM, databases, and billing systems, should be checked. Your business is stored on those servers, so if they are encrypted, we have a long road ahead of us.
Rescue What Can Be Saved
It crucial to being by validating which machines in the environment are NOT infected. Once this has been done, additional scans on those machines should be conducted to ensure this accuracy. Upon verification of this, you should move those machines to a “safe” network and establish specific connectivity for those business-critical machines.
Recover Environment
If you have good backups that managed to survive the attack, resist any temptation to start immediate restores. There is no sense in restoring what is only going to get re-encrypted. Also, if the threat actors still have a foothold, starting restores can tip them off to the location of your backups. Restoring too soon puts your backup data at risk.
Begin by restoring your backups to a new/fenced environment, followed by performing an additional scan on the restore to validate that the backups do not contain malicious code. Following this, you’ll want to verify the functionality of said backups, and establish specific connectivity to restored servers for business-critical functions.
Remediate Environment
To begin the final stages of remediation, it’s important to work with insurance/law enforcement to remove old servers after forensics. You can now establish the root cause, as well as how you can better protect your organization from future attacks with environmental enhancements/re-architecture.